How to check your website for polyfill[.]io vulnerabilities
A third party has taken over polyfill[.]io and appears to be delivering malicious JavaScript code. The malware being delivered by polyfill[.]io (the Payload) has affected more than 100,000 websites, and it’s important to verify that yours is not one of them. This document helps you verify that your website is not affected and correct it if you discover that it is.
This verification may require more than development staff. PageBuilder bundles are just one possible location for the Payload. It’s important to remember to check all possible locations.
What is polyfill[.]io?
Arc XP urges users not to visit polyfill[.]io, or any other site that hosts or serves malicious code. If you do visit that site, understand that you do so at your own risk and against our recommendations.
“Polyfill” is a term to describe JavaScript code that is deployed, usually in client-side web code, which augments the existing behavior of the web browser’s own JavaScript. Historically, browser compatibility issues have been challenging, and in order to make modern web applications functional in older browsers as these technologies have emerged, basic functions like Array.includes() (a function that determines whether the contents of an array include a specific value) were sometimes missing or different from what the developer originally intended. The term simply refers to a piece of code that makes all browsers work the same for that piece of code.
At one point, an open-source product called “polyfill[.]io” was distributed that was very helpful. It could detect which browser a user was using, and the developer could use this service to custom-tailor the polyfills for their code to only those that the user needed. This was helpful because it resulted in smaller bundles and reduced code complexity.
At some point, the maintainer of that project moved on to other ventures and transferred control of the project to another third party. Unfortunately, that third party appears to be delivering malicious code bundles from that service. A good deal of reporting (“See Also” below) outlines how this suspicious code may very well be malicious and could be violating privacy or security for web users.
Arc XP recommends that you quickly find and eliminate any references to this now-malicious service.
How can I find the malicious service?
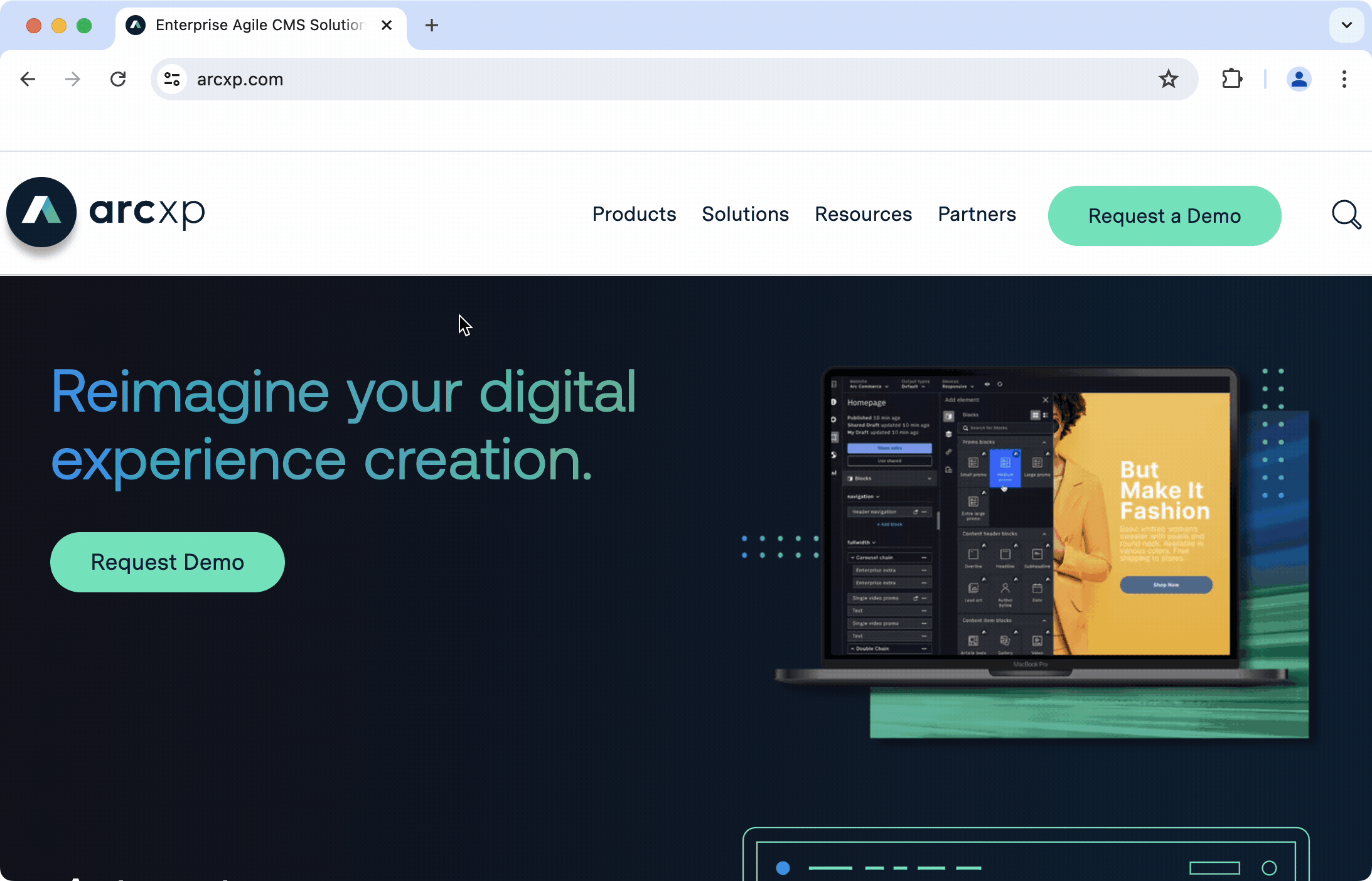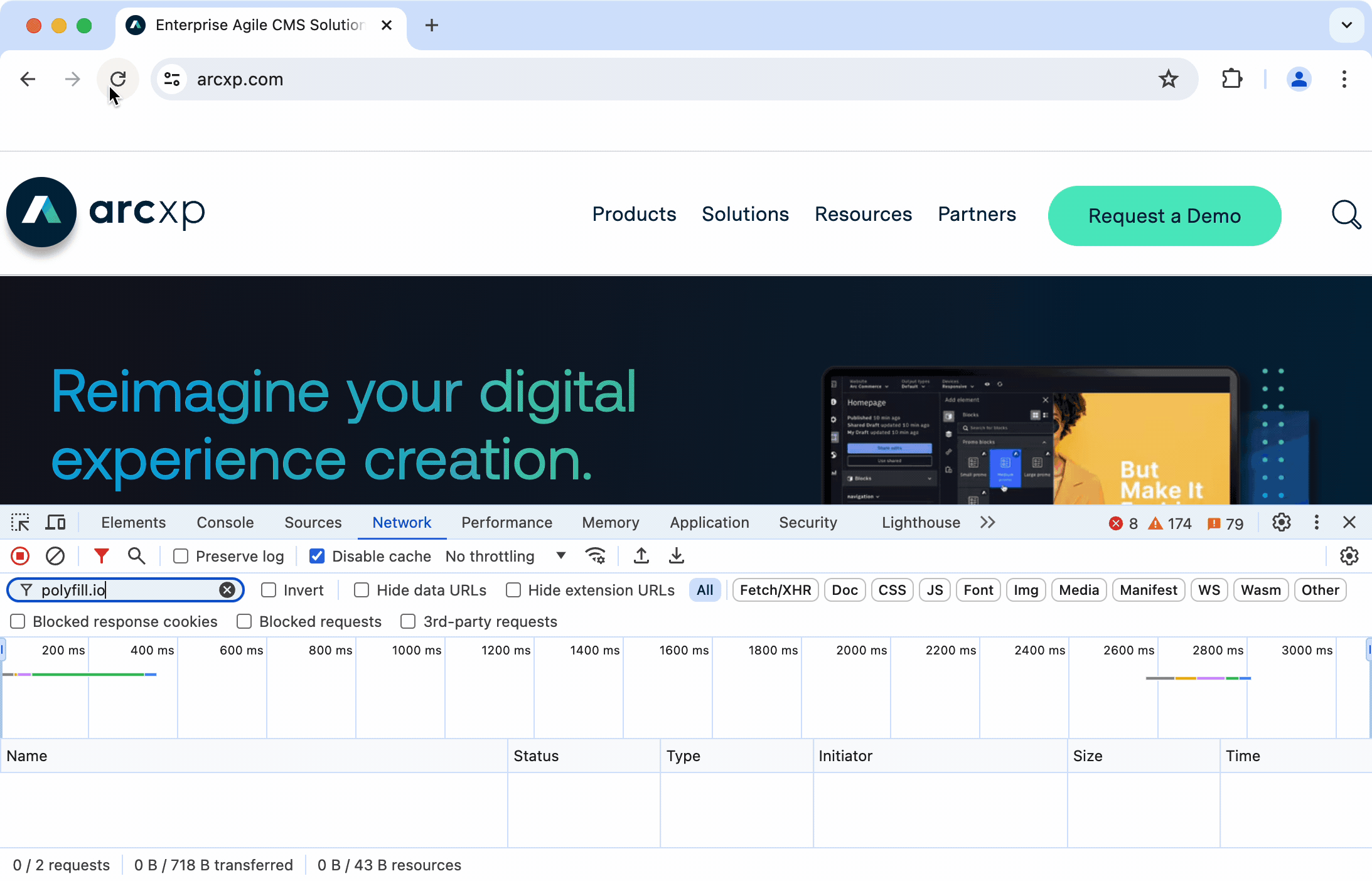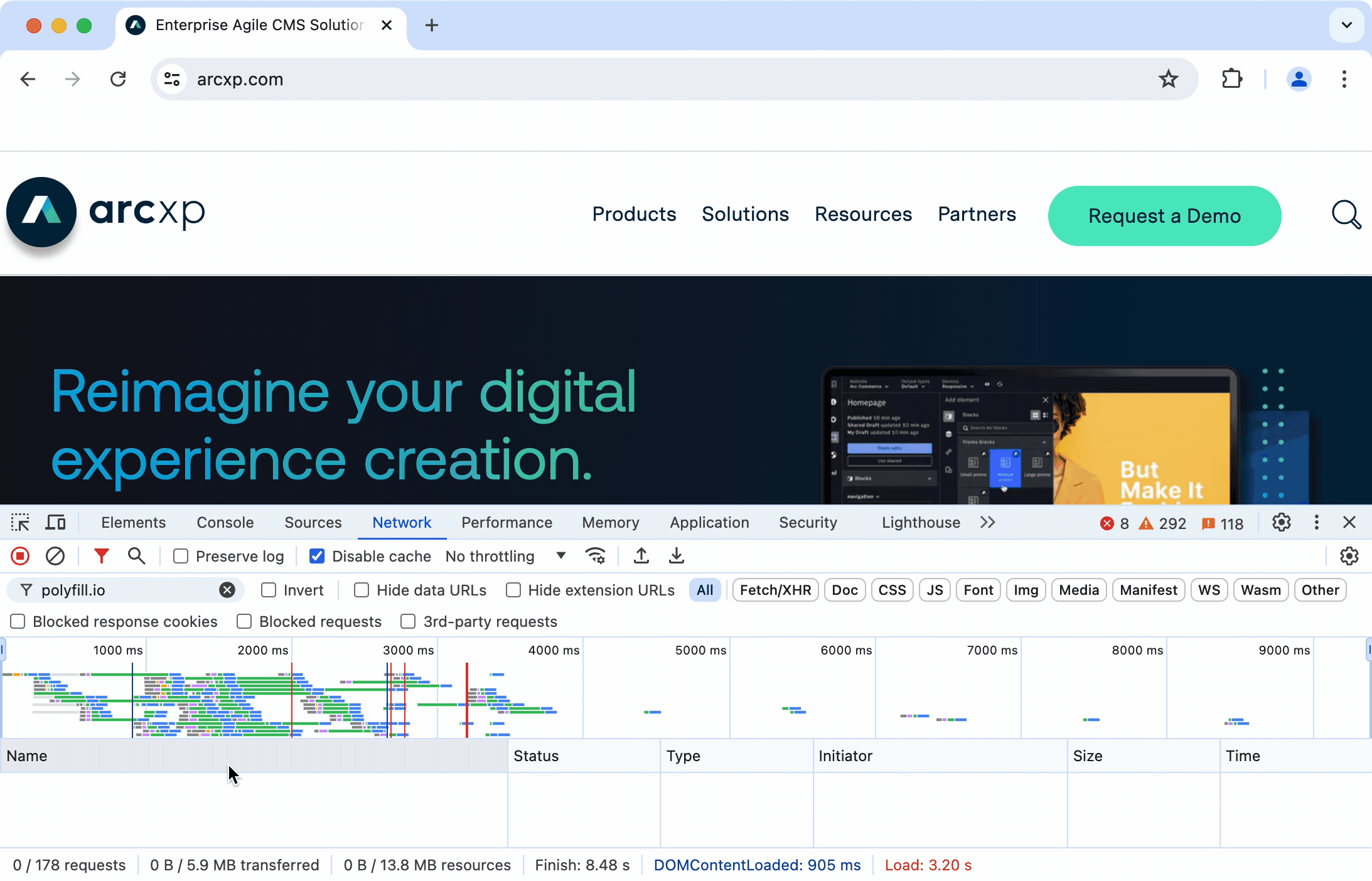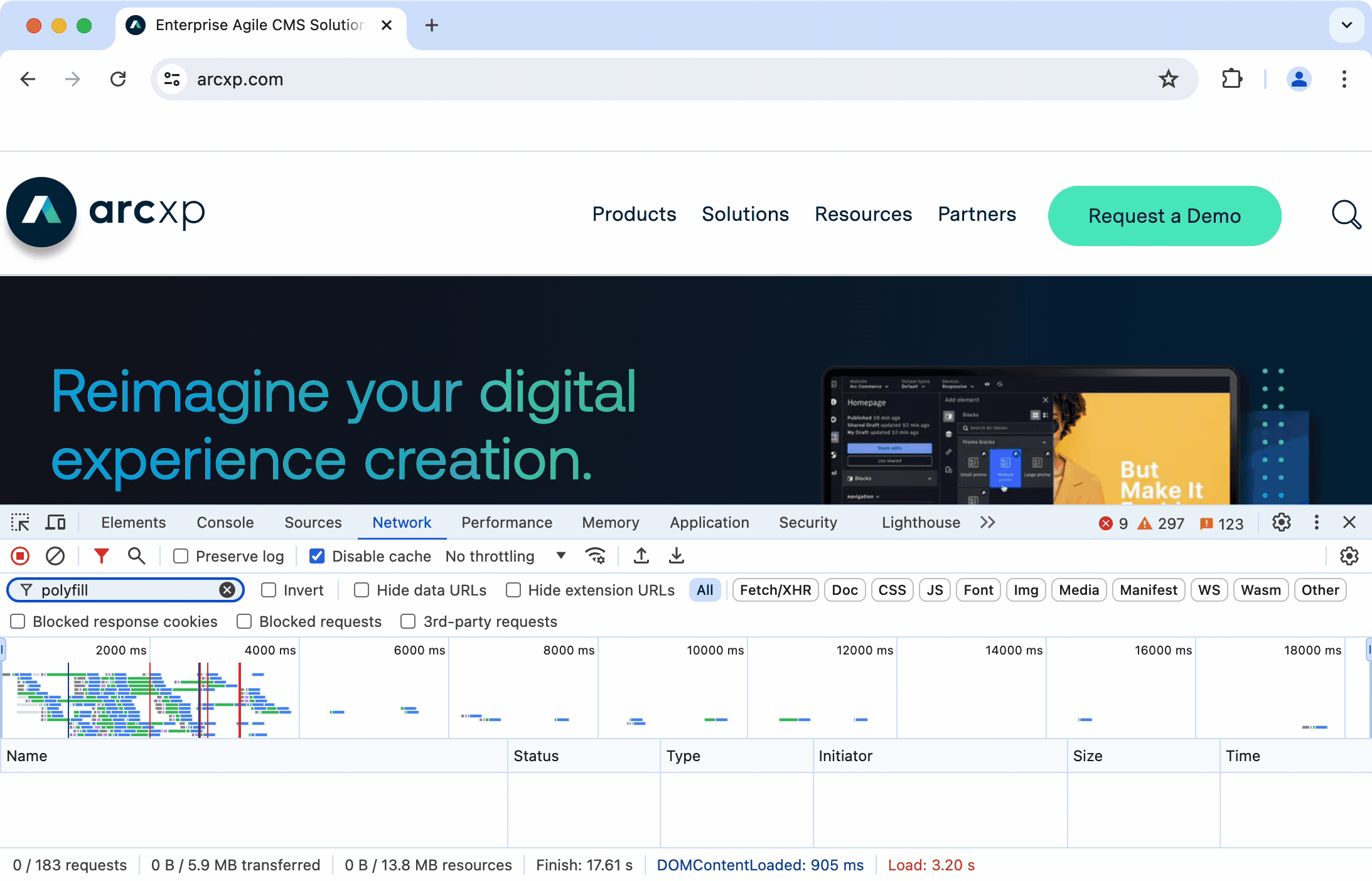
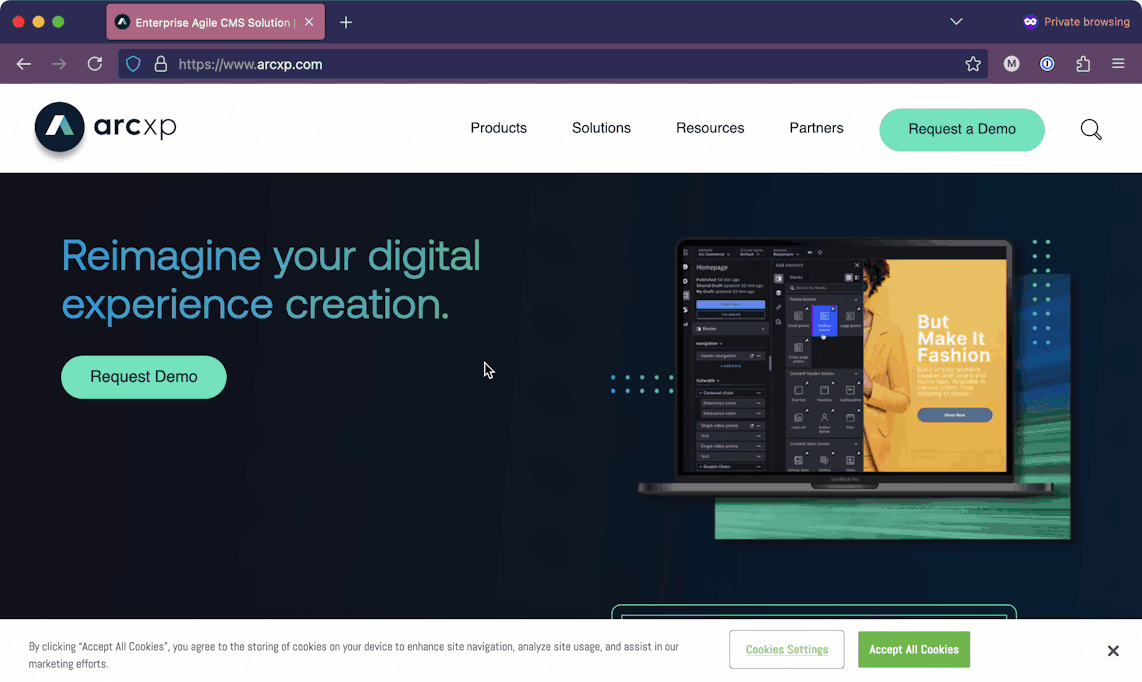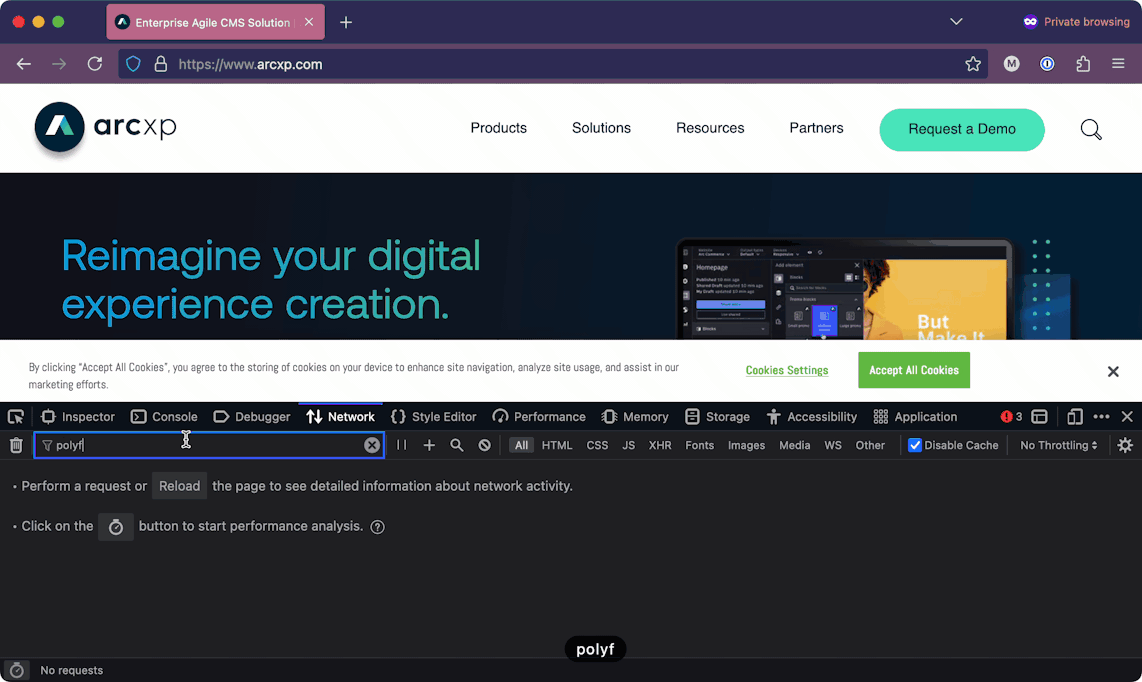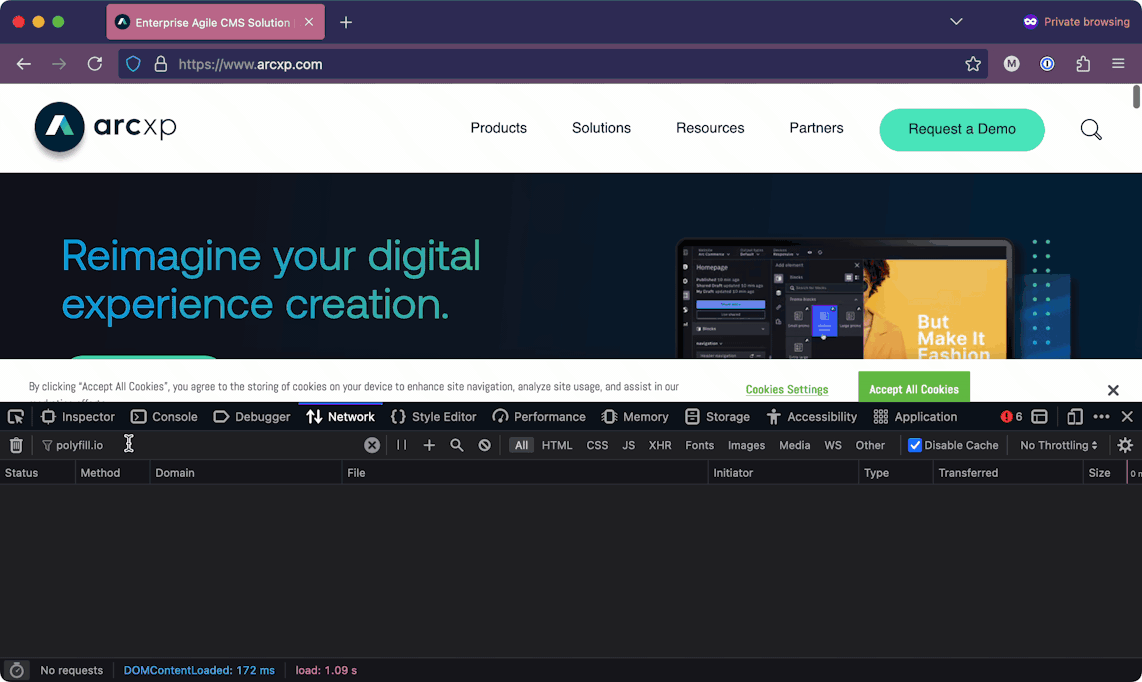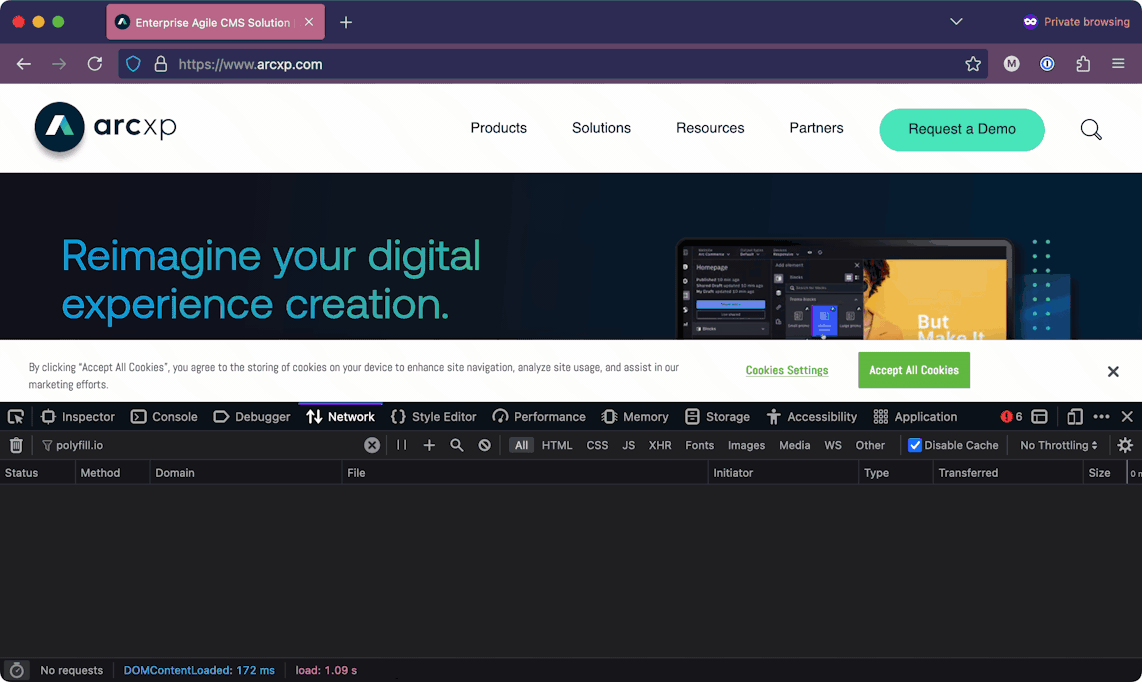
The best way to find malicious service is to monitor the network requests that are being made on your site. You can do this by looking in the network tab of your browser. The network tab can vary by browser, but the following table provides instructions on how to access these on the three major browsers today:
Browser | Hotkey for Network tab | Animated screenshot | |
Chrome and Edge |
For Chrome, you will then need to click the network tab |
| |
Firefox |
|
|
Where should I look to fix this?
The Payload may be present in a variety of locations:
In your PageBuilder bundles
In your HTML blocks on articles in Composer
In Themes v2, if you are deploying with a version lower than 2.2.1 or have copied the default output-type block to customize from a version lower than 2.2.1, then look in the <head> of your default output-type.
In Themes v1, if you are deploying with a version lower than 1.33 or have copied the default output-type block to customize from a version lower than 1.33, then look in the <head> of your default output-type.
In Custom Embeds, also known as Power Ups
In any of your Tag Manager code hosted by third-party services, such as
Google Tag Manager
Adobe Tag Manager
In many organizations, these various locations are maintained by different personnel. It is important to collaborate across your team to find and remove this Payload if you find it on your site.
Don’t stop at just one page on your site. As many Arc XP clients use different templates for different page types, it may be necessary for you to visit several pages to determine whether the Payload is present.
What about the Arc XP platform?
Arc XP has performed several thorough reviews to verify that all supported versions of our products and services do not contain the Payload.
How do I remove the Payload?
For PageBuilder bundles and Custom Embeds (also known as Power Ups)
Find instances of the Payload and remove them
Deploy the new version with the Payload removed
Terminate the old version of the bundle to void cached copies
If you do not perform this step, it could take time for your changes to be reflected on your website
For HTML blocks
Identify the affected content
Update the content, removing all instances of the Payload
For Tag Managers
Modify and deploy updates to all Tag Managers, removing the payload
If you are using or have copied from a Themes block with a v2 version lower than 2.2.1 or a v1 version lower than 1.33, then update to the latest block or review and fix the output-type in your copied code.
It is recommended that you clear your browser cache after deploying fixes in order to accurately see what is being delivered to web users.