Server-side paywall (SSP) best practices
This guide provides recommended practices for implementing and managing server-side paywall (SSP) in Arc XP.
SSP is a standardized Arc XP feature. To enable SSP, contact Arc XP Customer Support and provide the following information:
Organization name
Site ID
Environment (for example, Sandbox, Production)
Login URL
Inclusion/Exclusion regex for defining where SSP should apply
External Identity Provider details
After we enable SSP, it's configured at the CDN/Delivery layer for your site.
SSP uses entitlements (also called variants) to determine how different users experience your site.
Entitlements define differentiated renderings of a site, assigned based on resolver query string parameter (QSP) matches.
They do not map directly to a user group or identity but provide alternate user experiences.
A variant is the entitlement value stored in the server-side paywall cookie, which maps to the QSP within PageBuilder Engine resolvers.
Limits
You're allowed two entitlements per site delivery configuration. Entitlements are limited to preserve cache performance. Excessive variants or QSPs degrade caching efficiency.
When designing entitlements, consider how user groups overlap in content access.
Group users logically: for example, monthly subscribers, gift users, and allow-listed organizations may share the same entitlement.
Use for time-limited experiences: you can update entitlements dynamically through client-side tracking beacons or other mechanisms (for example, granting premium access for 10 articles, then downgrading access).
Avoid using entitlements as defaults: standard (anonymous or new) user experience should remain the default; entitlements should only define alternate status.
The following diagram illustrates how to effectively use entitlements.
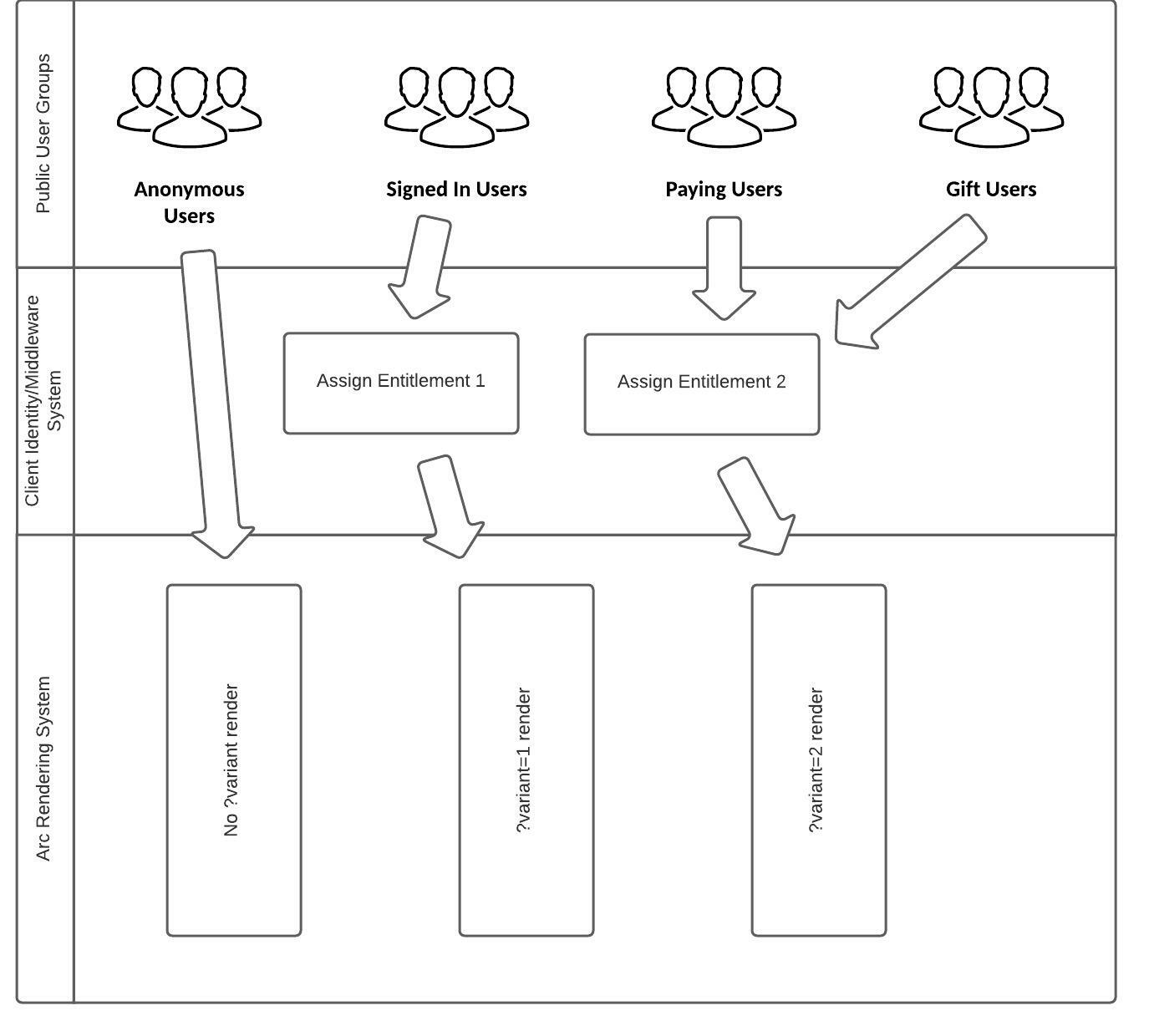 |
You can apply SSP per-path to any content served by your PageBuilder Engine bundle.
Ensure paywalls content provides enough visible text for crawlers to understand the page.
For hard paywalls, the search engine version should match the non-logged-in experience.
User-agent whitelisting and reverse DNS verification are not supported by Arc XP's CDN vendor and introduce security risks.
Configure Composer preview to use your Trident domain as the preview URL.
Add a variant=<QSP> parameter to preview specific entitlements.
Partners and providers requiring access must support the use of an SSP cookie to retrieve the desired entitlement experience.
You can configure the entitlement expiration separately from the cookie expiration. The entitle expiry controls when a user is redirected to login. Use modal or silent login flows to refresh the SSP cookie during active sessions. Set cookie expiration to the maximum idle time allowed before re-authentication.
Whitelisting: User-agent and IP whitelisting are not permitted as bypass mechanisms.
Metered paywalls: SSP does not support metered models (client-side logic is required).
Audience Targeting: Some Arc XP features, such as Audience Targeting, may have limitations when SSP is enabled.